Pakistan-based group uses 7th Pay Commission to target Indian govt officials: FireEye
The emails were allegedly sent to government officials from timesofindiaa.in, a fake news domain registered by the attackers.
Days after Kaspersky claimed Indian government sites were compromised by a cyberespionage group, cybersecurity firm FireEye, Inc has claimed that a fake news website was used to sent spear phishing emails to Indian government officials as part of cyber attacks by a suspected Pakistan-based group.
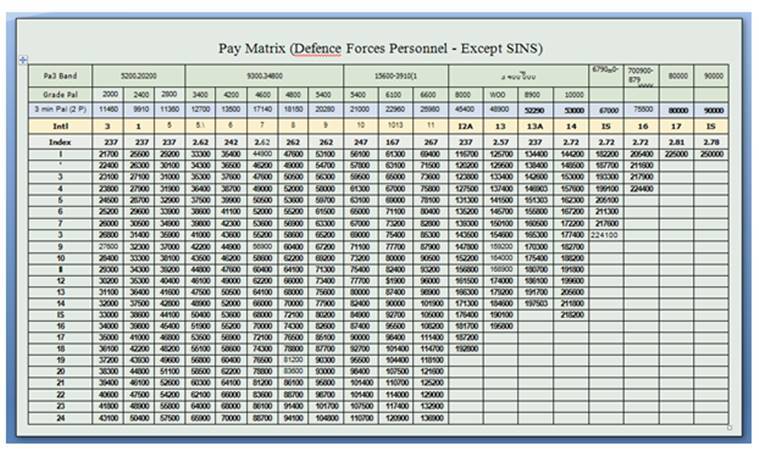
“On May 18, 2016 the group registered a fake news website and sent spear phishing emails to Indian government officials. The emails referenced the Indian Government’s 7th Central Pay Commission, a topic of interest among officials,”a blog posted by the company claimed.
“There’s no silver bullet to fend off advanced cyber attacks. It’s critical for Indian organisations to bring together the technology, expertise and threat intelligence necessary to quickly detect and respond to these attacks,” said Bryce Boland, Chief Technology Officer for Asia Pacific at FireEye.
The company claimed the emails were sent to government officials from timesofindiaa.in, a fake news domain registered by the attackers. The emails has a malicious Microsoft Word document attached, requesting the recipient to open it.
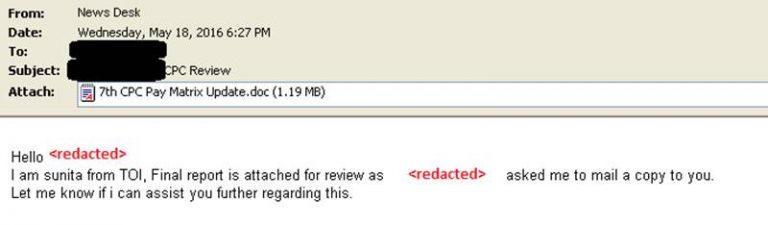
FireEye said the attachment was designed to create a backdoor called the Breach Remote Administration Tool (BreachRAT)” and said it has not observed this malicious tool being used by these threat actors before. “It allows the attacks to download and run new programs, upload files from the victims’ systems to the attackers’ servers, and a variety of other functions.
The suspected Pakistan-based threat group has been active for several years, conducting suspected intelligence collection operations against South Asian political and military targets, claimed FireEye. “The group is the same that FireEye revealed in March 2016 to have conducted cyber attacks against Indian targets and Pakistani dissidents since 2013. They were observed using malicious documents hosted on websites about the Indian Army, instead of sending these documents directly as an email attachment,”the post claimed, adding that infrastructure used by the group is the same in both attacks.
Source : indianexpress.com

Leave a Reply